A Clever Russian Phishing Attack Using Fake State Department Employees

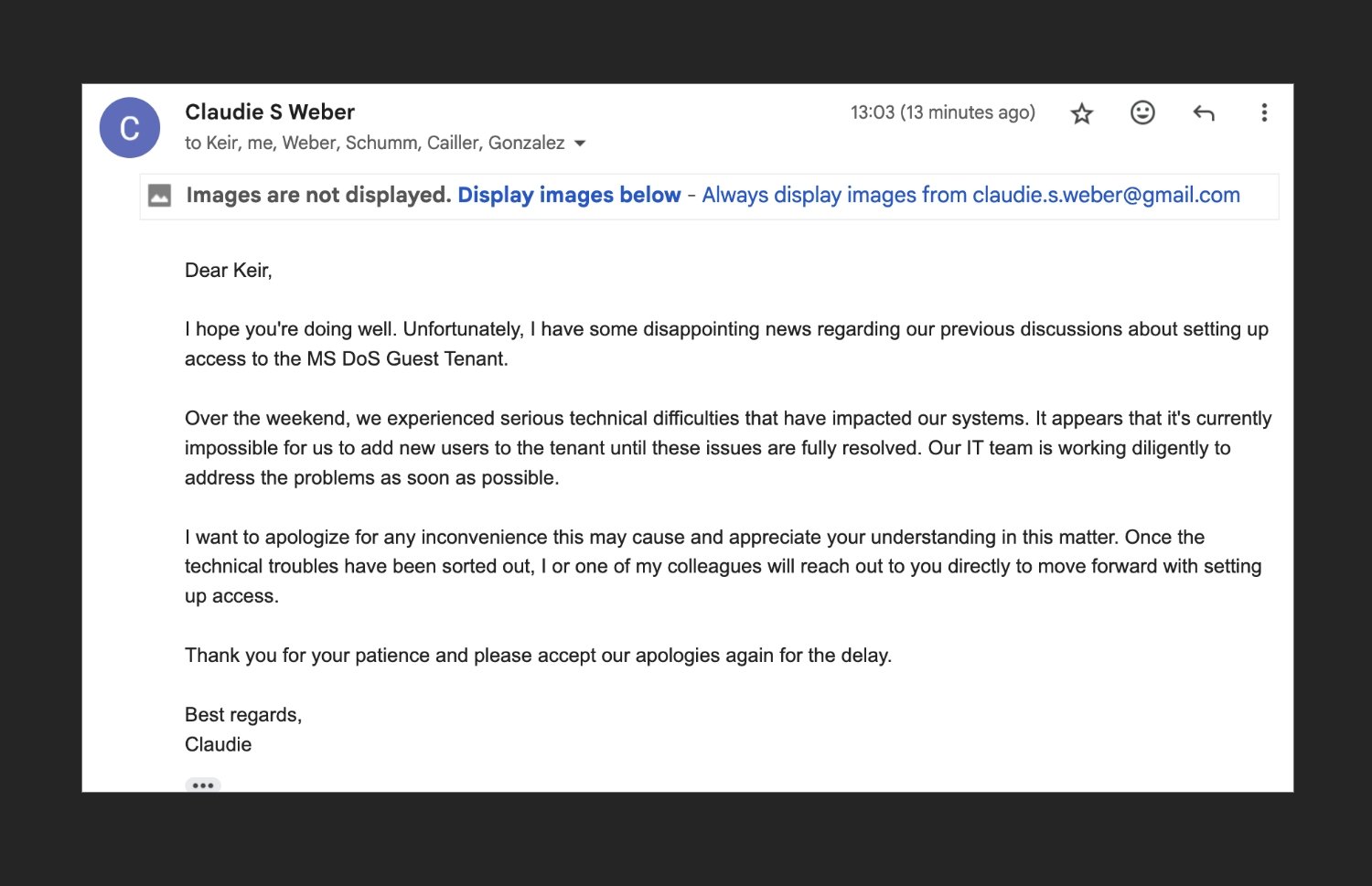
Claudy Weber is a major program advisor to the US State Department. I called me via email in May, looking to discuss “recent developments” and copy many of her colleagues in the departments. This is not unusual for people in the line of work. What was a little less common was that “Claudy” was not present, and none of her colleagues did with the addresses of the Ministry of Foreign Affairs. The approach was part of an accurate plan to break my Gmail account. It seems that he succeeded.
For Russian professional observers like me, the issue of unwanted Internet interest comes with the job. Raw attempts of piracy and hunting are more or somewhat less, and from time to time we face something new or smart. Once again in 2019, a whistle in an online deception campaign was blown up by LinkedIn, which was the first documented example of the face created by Deepfake that is used as part of this process. Two years later, the well -made brown hunting attempt was half a second away from clicking on a deceptive link that seemed to remind the date of the actual and standard specialist.
Claudy Weber is a major program advisor to the US State Department. I called me via email in May, looking to discuss “recent developments” and copy many of her colleagues in the departments. This is not unusual for people in the line of work. What was a little less common was that “Claudy” was not present, and none of her colleagues did with the addresses of the Ministry of Foreign Affairs. The approach was part of an accurate plan to break my Gmail account. It seems that he succeeded.
For Russian professional observers like me, the issue of unwanted Internet interest comes with the job. Raw attempts of piracy and hunting are more or somewhat less, and from time to time we face something new or smart. Once again in 2019, a whistle in an online deception campaign was blown up by LinkedIn, which was the first documented example of the face created by Deepfake that is used as part of this process. Two years later, the well -made brown hunting attempt was half a second away from clicking on a deceptive link that seemed to remind the date of the actual and standard specialist.
But Claudy’s efforts were different again. Carefully gathered the operators behind this name, roughly a number of different columns of reasonable, and unlike previous occasions, they did not put forward. For example, they clearly knew that the first thing I would do is write to her “colleagues” in them State.gov Addresses to see if they were present – but they also knew, which I did not do, that the US State Department’s email server accepts all incoming messages and will not show you a mistake if you are writing to people who are not present.
An email to “Claudie Weber” showing her and fake US State Department addresses.
This was followed by a slow, patient and successful process at the end to train me to open the back door for all of my email messages.
My e -mail account has been described in detail by the Citizen Laboratory at the University of Toronto, an organization dedicated to protecting civil society from the state’s campaigns of this type, and you can read some traffic via email with “Claudi” in their report. The group of threats from Google’s threats reported the operation and linked it to others that it is in principle to the Russian foreign intelligence service.
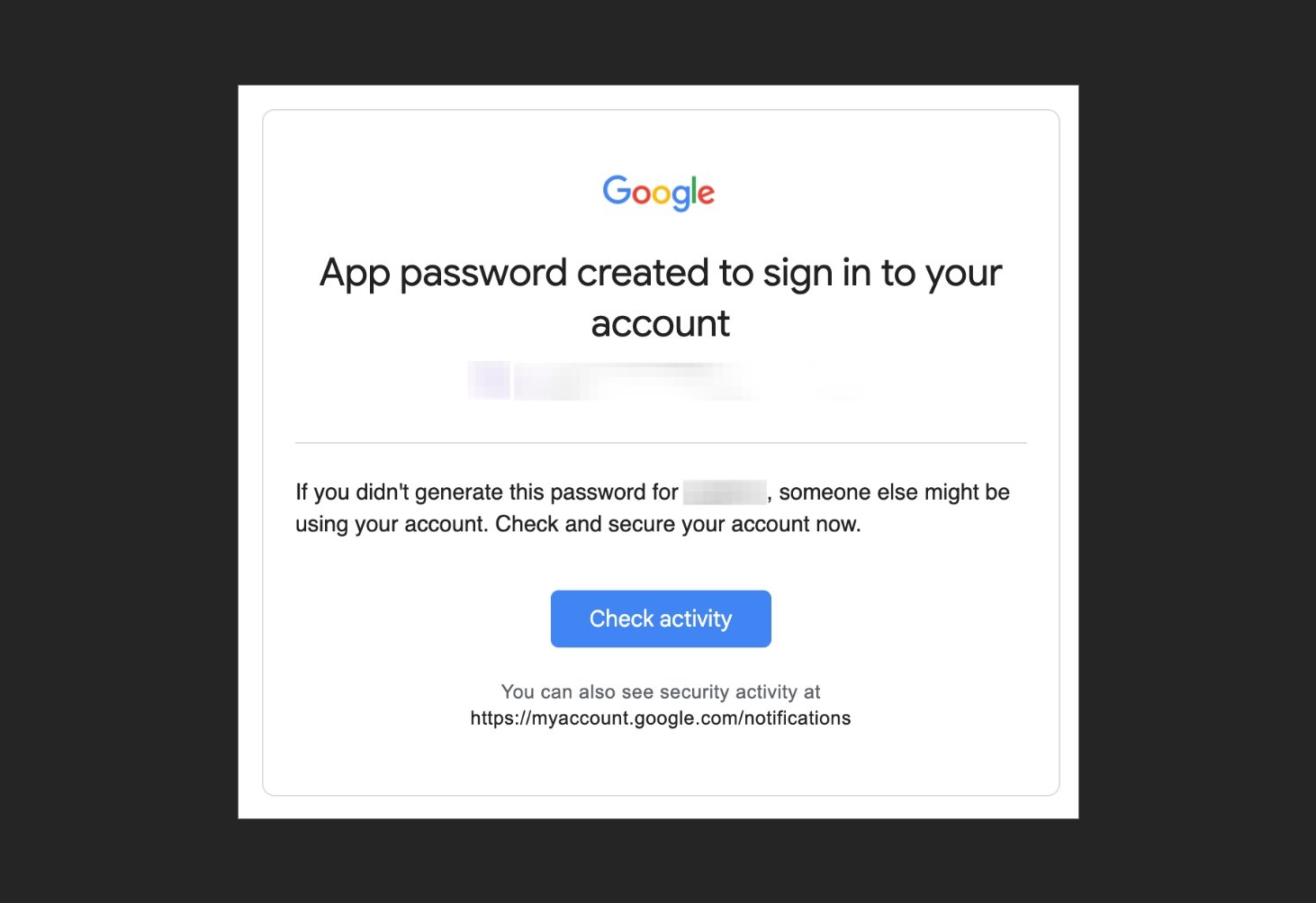
Use the attack on Gmail and other apps called application password, or ASP. This is a way to create a special password so that you can still use old or less safety applications that do not support modern safety protocols.
This is where the problem lies: ASPS is a widely available way to overcome all security precautions that are all informed of all of them insisting on making sure that they are in place, such as sending verification codes to our phones. This feature is supported by Microsoft, Apple, Google and other platforms as an artistic alternative to an artistic alternative when other safety systems do not work, with easy -to -use warnings about the danger of this tool.
More importantly, the penetration did not take advantage of some technical weakness in the program. Google also indicated, “There was no defect in Gmail itself,” Instead, “the attackers misused legal jobs.” This is true: The ASP setting was done exactly as intended. The attack has worked by convincing me to prepare a road in my integrated account according to the design, rather than overcoming security and collapse. In the most literal sense, this back door to our email accounts is not a mistake but an advantage.
But there is a problem with that. The fact that there is a widely available option to overcome safety precautions today and throw your open account wide, was an unexpected discovery not only for me, but also for anyone who spoke to him and not deep in the field of cybersecurity.
Google’s password notification.
So, Google to say that “there is no weakness associated with the passwords of the Google application”, again, technically correct, but it is likely to be very misleading in terms of the ease of exploitation of ASPS-as it is clear from my condition, however, there may be many others now. (It seems that I am the first person to be announced in this way, but I am sure I will not be the last.)
Google also showed, users get an email for notification when creating this password. But this is intended for limited use when you already know that you are preparing one, whether you have been deceived in doing this or not.
Since everything was working as intended, there was no way that I could see nothing was wrong. Google credit, its safety systems were that eventually noticed that something was wrong and caused my account to freeze. After recovering my account, I found a deeply buried notification in the safety settings about logging in from a suspicious address – eight days before my Google account imprisoned without any warning.
The way the digital security platforms tightened while maintaining the option to use ASPS for communication is like investing in heavy new locks for your front door but leaving the side door open to people who do not have the keys. Since it involves a new smart attack that can affect almost anyone, I have created my condition a great deal of attention in the media specialized in cybersecurity. It is normal for other institutions to be more amazing in identifying the security problem. As Sophos, there is another cybersecurity security company, who politely noticed a warning to customers on June 18: “The potential impact of creating the application password is not clarified and provided with the third party in the construction process.”
In other words, what would really help was a warning during the process of creating ASPS for what they were exactly and what they were doing, which would have alerted me to what was going on. Google properly indicated a warning on these lines in their auxiliary files. But this does not help if you do not go to these auxiliary files-because, as in my case, your striker gave an authentic guide to him to walk in this process.
The real heroes of this story are in the Citizen Laboratory-in particular, the teacher of privacy and security John Scott Rilton. John, along with Reuters journalists Rafael Satter and James Pearson, who helped me collect what happened when all I could see was that Google had froze my account (and in one case he told me that this is due to “political violations”). They were the ones who used Google’s professional contacts to try to help me.
The citizen’s laboratory describes himself as a “multidisciplinary laboratory” that focuses on research in information technology and human rights. But their investigations into digital espionage against civil society – and their efforts to protect the privacy of citizens and other rights against companies and state agencies – are invaluable for people like me who direct their finger to bad guys such as the Russian state, but they have no support from governments or strong institutions behind them.
Many people asked me if I was concerned about what the attackers would do with the messages he copied from my account. One of the next step is that any e -mail messages that were stolen from the account will be used in the outstanding breach attack, as the infiltrators transfer them to Western agents or sympathizers with Russia for their release as a “leak” aimed at distorting the Moscow opponents.
In 2023, when the Scottish parliament and Russian critic Stewart McDonald likened it, it took less than 48 hours after announcing that it was penetrated by Russia to British activist Craig Murray to show off that he had received McDonald’s emails.
The so-called leakage is usually a mixture of original messages and files, some of which have been changed, while others were simply invented-in addition to malware and viruses to injure any curious person enough to download them. The goal can be to draw for me and the institutions with which I work as two Kricks, the new Nazis, spies, researchers, or aggressors of materials, puppies, or all of the above. But this means that there is a little benefit in worrying about anything that is likely to be embarrassing in my emails – if the infiltrators do not find what they hope for, they will make it anyway.
At the present time, Russia’s consolidation on social media is already busy with their copies of what I am and what happened. There is a fixed pattern where it takes 24 hours after something for their stories to go out to publish – and then, the same lines are repeated for the word via different media and different languages. Some of the realistic figures in the business in Russia were also outperforming the “funny” penetration. But this is not much different from the background noise of the lies and the misuse that someone takes in the line of my work is rejected by it.
What is much more important in this case is the number of other people around the world can be exposed to the same threat of security and they do not know anything about it. Now that the power of this tool has been proven, Cyber researchers expect to use it on a larger scale. This means that it can be misused not only against people who have made enemies in Russia, like me, but also ordinary users who may not consider themselves in danger. This may be for electronic crimes, low -grade intrusion, or just settling grades.
The infiltrators carefully did a reasonable story.
In my case, the attackers put an unusual amount of time, effort and patience in building deception. For any reason, they decided that I deserve all this effort – or perhaps they were frustrated after many previous failed efforts over many years.
But anyone is not automatic like me – perhaps because it is not in a group of work that he sees routinely targeted – can be taken into a less developed deception campaign. Maybe we all have friends and relatives, especially the oldest, who were taken in fraud that seemed clearly clear.
If they know how, readers should check if this type of password has been prepared on their accounts. If they are worried, there are options such as Google’s advanced protection program, which prohibits this attack method and others. But in any case, Google and other companies should ensure that the risk of this account feature is widely understood by ordinary users.
When the attacks succeed, it is also important for more people to talk about them. It is understood that individuals who are deceived in this way sometimes hesitate to progress and share details. Anyone who is thicker than me is embarrassing-and feels slightly stupid than overcoming it. But it is necessary to share the largest possible. Our collective security deserves more than one individual editor for one person.
Don’t miss more hot News like this! Click here to discover the latest in Politics news!
2025-07-02 18:52:00